HarmonyOS-powered distributed devices ensure that the right person uses the right data through the right device.
- Ensure the right person by performing distributed collaborative identity authentication.
- Ensure the right device by building a trusted operating environment on the distributed device.
- Ensure the right data by implementing classified and hierarchical management of data transmitted across devices.
Right Person
In the distributed scenario, the right person refers to an authenticated user who accesses the data or uses the service. The right person is the prerequisite for preventing illegal data access or user privacy breach. HarmonyOS implements distributed collaborative identity authentication in the following ways:
- Zero-trust model: Implements user authentication and data access control. When a user attempts to access data across devices or perform a service operation with a high security level (for example, operating a security protection device), HarmonyOS authenticates the user to ensure that the user is authorized to perform the operation.
- Multi-factor authentication: Associates authentication credentials that identify the same user on different devices to improve authentication accuracy.
- Collaborative authentication: Decouples identity authentication from hardware so that identity authentication and data collection can be done on different devices to implement resource pooling as well as capability collaboration and sharing. This allows the right device to do the right thing and makes it possible for devices with a high security level to assist devices with a low security level in authenticating users.
Right Device
In the distributed scenario, the right person using the right device is the prerequisite to safeguard effective user data security on virtual devices and prevent user privacy breach.
- Secure bootHarmonyOS ensures from the source that the system firmware and applications running on each virtual device from the source are intact and untampered with. With secure boot, HarmonyOS protects image packages of device vendors from being replaced maliciously, thereby ensuring user data security and privacy.
- TEEHarmonyOS provides a hardware-based Trusted Execution Environment (TEE) to prevent data leakage of sensitive personal data when they are stored or processed. As the hardware of distributed devices varies in security capabilities, security issues may arise if sensitive personal data of users is stored and processed by devices with a low security level. To address this issue, HarmonyOS uses formal verification methods, which are an effective mathematical approach to validate system correctness, to secure the TEE microkernel. This helps the microkernel successfully achieve a CC EAL5+ certification for a commercial OS kernel.
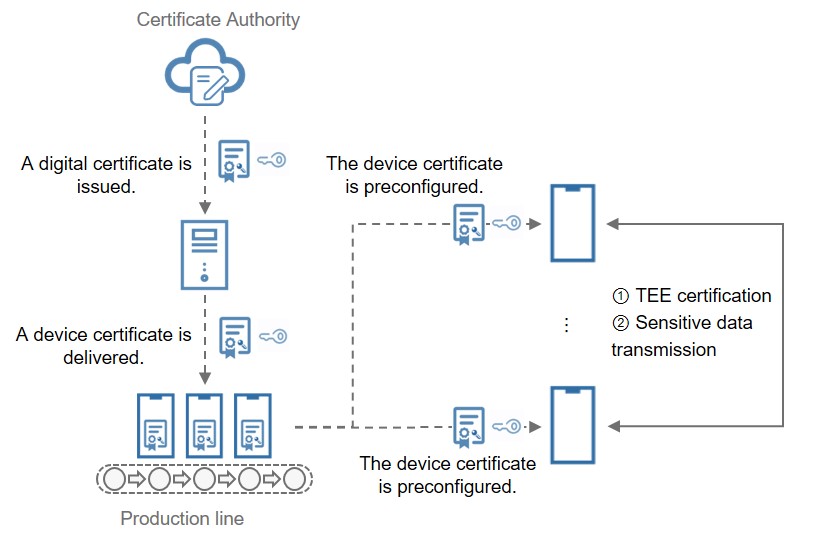
- Device certificate authenticationHarmonyOS preconfigures a public key infrastructure (PKI) device certificate in the TEE of a device so that the device can prove its security capabilities to other virtual devices. The device certificate ensures that the device is one that was manufactured legally. The certification is preconfigured during device production and proves that the device was manufactured legally. The private key of the certification is written and securely stored in the TEE and can only be used in the TEE. When sensitive user data (such as keys and encrypted biometrics) needs to be transmitted between devices, a secure channel is established between their TEEs only after the device security has been proven using the device certificate. Figure 1 shows how the device certificate is used.
Figure 1 Using the device certificate
Right Data
To ensure that the right data is used by the right person, HarmonyOS protects data security and privacy throughout the entire lifecycle, from data generation and storage to data use, transmission, and destruction. This ensures that personal data and privacy as well as confidential data (such as keys) are strictly protected against disclosure.
- Data generation: Data is categorized and classified in compliance with local laws and regulations, and different protection levels are configured for the data based on the classification. For data granted with a specific protection level, security protection is implemented based on the corresponding security policy throughout the entire lifecycle. The access control system of the super virtual device supports tag-based access control policies, which ensure that data can be stored, used, and transmitted only on virtual devices that are able to provide effective security protection.
- Data storage: Data with different security levels are stored in partitions with corresponding security protection capabilities to ensure data security. In addition, seamless cross-device key mobility and access control are supported throughout the lifecycle of keys for distributed, collaborative identity authentication and data sharing.
- Data usage: Sensitive user data can only be used in a hardware-based TEE of distributed virtual devices, thereby ensuring data security and privacy.
- Data transmission: To ensure secure data flow between virtual devices, each device must be reliable and trusted. Trust relationship is established among multiple virtual devices paired by using a HUAWEI ID. A secure channel will be established between virtual devices only after the trust relationship is verified, so that data can be transmitted securely. If two devices need to communicate with each other, they must be authenticated based on their identity credentials. After a successful authentication, an encrypted channel will be established for communication between the devices.
- Data destruction: Data destruction is implemented by destroying keys. Data is stored on virtual devices based on keys. To destruct data completely, you only need to destroy the keys protecting the data.
source : https://developer.harmonyos.com/en/docs/documentation/doc-guides/harmonyos-security-0000000000011934#section1576419151014